| Category | Responsibilities |
|---|---|
| Customer Data | Data management, including encryption, storage, and access controls, is handled by AWS, which also ensures the security of the underlying infrastructure. |
| Platforms | Securing and configuring AWS applications includes patching and managing access controls. |
| Applications | Ensuring the security of applications through authentication, encryption, and regular auditing, while AWS guarantees the availability and security of the underlying infrastructure. |
| Identity and Access Management (IAM) | Enforcing IAM practices, creating and managing users, roles, and permissions, and setting up multifactor authentication. AWS provides tools and services for IAM and ensures service security. |
| Operating Systems | Managing and securing operating systems of VM or EC2 instances, including patching and vulnerability monitoring. AWS manages physical hosts and hypervisors. |
| Network Configuration | Setting up network configurations such as VPC settings, subnet structures, security group policies, and network ACLs, with AWS ensuring the security and availability of the underlying network infrastructure. |
| Firewall Configuration | Setting up firewalls, security group rules, and network ACLs to manage traffic flow while AWS furnishes the necessary physical network infrastructure and firewalls for optimal configuration. |
| Client-Side Data Encryption | Ensuring data encryption prior to uploading to AWS services, managing encryption keys, and implementing stringent access controls while AWS furnishes secure infrastructure and encryption alternatives. |
| Data Integrity Authentication | Ensuring data integrity and authenticity through hashing, signing, and verifying data. AWS offers features like AWS CloudTrail for monitoring and logging. |
| Server-Side Encryption | Choosing and managing server-side encryption options for data stored within AWS services. AWS ensures proper implementation and maintenance of encryption features. |
| Networking Traffic Protection | Implementing traffic protection measures like SSL/TLS encryption, VPNs, or AWS Direct Connect. AWS ensures secure and resilient network infrastructure. |
Summary
The blog encapsulates the AWS Shared Responsibility Model, emphasizing collaborative security efforts between AWS and customers. Explore how AWS ensures infrastructure security while you manage data protection. Furthermore, it offers practical insights into implementing this model and highlights its significance in fostering a robust AWS environment essential for business continuity.
Table of Contents
Introduction
With evolving technology, more and more organizations are moving their data to the cloud. Eventually, with increasing cloud adoption, the range of cloud vulnerabilities has become a significant source of threats. Your cloud environment can be breached for any reason – it can be due to misconfiguration, weak encryption, shared technology vulnerabilities, account hijacking, and more. Capturing headlines with sophisticated scams and unsuspecting victims has become a major cause of concern for cloud service providers as well as customers.
However, what these stories often fail to emphasize is a crucial fact: in most cases, it’s the customer, not the cloud service provider, who bears responsibility and the associated loss from these breaches due to inadequate security controls.
According to Gartner, by 2025, a staggering 99% of cloud security failures will stem from customers. This underscores the importance of understanding and actively managing security responsibilities.
The AWS shared Responsibility Model outlines security & compliance responsibilities between the cloud service provider and customers to ensure accountability. While AWS offers strong security measures, customers must enforce and manage security controls to protect their data actively. Let’s explore this shared responsibility model and how responsibilities are divided between AWS and its customers.
What is the AWS Shared Responsibility Model?
The AWS shared responsibility model defines the allocation of security & compliance duties between AWS and its customers.
AWS is accountable for ensuring the “security of the cloud”, safeguarding its infrastructure and services. This infrastructure encompasses the hardware, software, networking, and facilities necessary for operating AWS Cloud services.
Moreover, AWS also prioritizes,
✔ Sustainability of the Cloud
AWS prioritizes sustainability in the cloud by investing in efficient technology and serving to minimize energy usage and environmental impact. It encourages resource sharing among cloud workloads to reduce further energy consumption. Additionally, it offers options for customers to migrate to even more efficient systems and leverage cloud services.
✔ Resilience of the Cloud
AWS also emphasizes resilience by ensuring infrastructure reliability, meeting service agreements, and establishing multiple isolated availability zones within each region, interconnected by high-speed networks, to safeguard against power outages and natural disasters and ensure smooth application operation.

Conversely, customers are responsible for maintaining “security in the cloud,” which involves securely configuring and utilizing AWS resources and protecting their data and applications. The customer’s responsibilities with AWS depend on the services they choose.
Moreover, customers can also prioritize,
✔ Sustainability in the Cloud
Cloud sustainability emphasizes minimizing energy consumption and optimizing efficiency across every aspect of a workload. It includes choosing efficient programming languages, algorithms, and data storage techniques, deploying appropriately sized compute infrastructure, and minimizing high-powered hardware requirements.
✔ Resilience in the Cloud
Your responsibilities on AWS depend on the services you choose. For services like Amazon EC2, customers handle resiliency tasks like deploying across Availability Zones and implementing self-healing. AWS manages infrastructure for managed services like Amazon S3, but customers handle data resiliency tasks like backup and replication. Deploying across Availability Zones ensures high availability and forms part of an AWS disaster recovery strategy to protect against outages and disasters.
Elements of the Amazon Shared Responsibility Model
We’ve divided the responsibilities between customers and AWS for your reference:
A. Customer Responsibilities [Security in the Cloud]
The AWS shared responsibility model outlines explicitly customers’ responsibilities, which are mentioned below for your reference.
B. AWS Responsibilites [Security of the Cloud]
The AWS shared responsibility model specifically outlines AWS’s responsibilities, which are mentioned below for your reference.
| Category | Responsibilities |
|---|---|
| Software Management | Ensuring the security and integrity of software powering AWS services, including patching, updates, and maintenance. |
| Compute, Storage, Database, and Networking Infrastructure | Managing underlying infrastructure, including servers, storage devices, database servers, and network components, ensuring availability and performance. |
| Hardware and Global Infrastructure | Overseeing global data centers, servers, networking gear, and storage devices to ensure both reliability and security. |
| Regions, Availability Zones, and Edge Locations | Overseeing management and reliability of global infrastructure, including physical locations, isolated data centers (Availability Zones), and edge locations. |
Types of Controls
The shared responsibility between AWS and the customer extends to IT controls, which both parties manage, operate, and verify. Examples of controls managed by AWS, customers, and both include
A. Inherited Controls: The AWS shared responsibility model has inherited controls handled entirely by AWS, like
- Physical and Environmental controls
B. Shared Controls: The AWS shared responsibility model, has shared controls that refer to standards set by AWS for the infrastructure, which customers implement while utilizing AWS services. Examples include:
- Patch Management: AWS fixes infrastructure flaws, and customers handle OS and app patches.
- Configuration Management: AWS configures infrastructure, customers handle their systems.
- Awareness & Training: AWS provides training for its employees, while customers are accountable for training their staff.
C. Customer-Specific Controls: Responsibilities are unique to customers and depend on their AWS-deployed applications.
- Service and Communications Protection or Zone Security: Protection managed by the customer necessitates data routing through secure environments.
AWS Shared Responsibility Models
AWS has formulated three main shared responsibility models that explain the boundaries of responsibility between AWS and customers, clarifying the extent of each party’s obligations.
A. Amazon Shared Responsibility Model for Infrastructure Services
The infrastructure service refers to a form of computing service in which AWS manages the fundamental virtualization infrastructure.
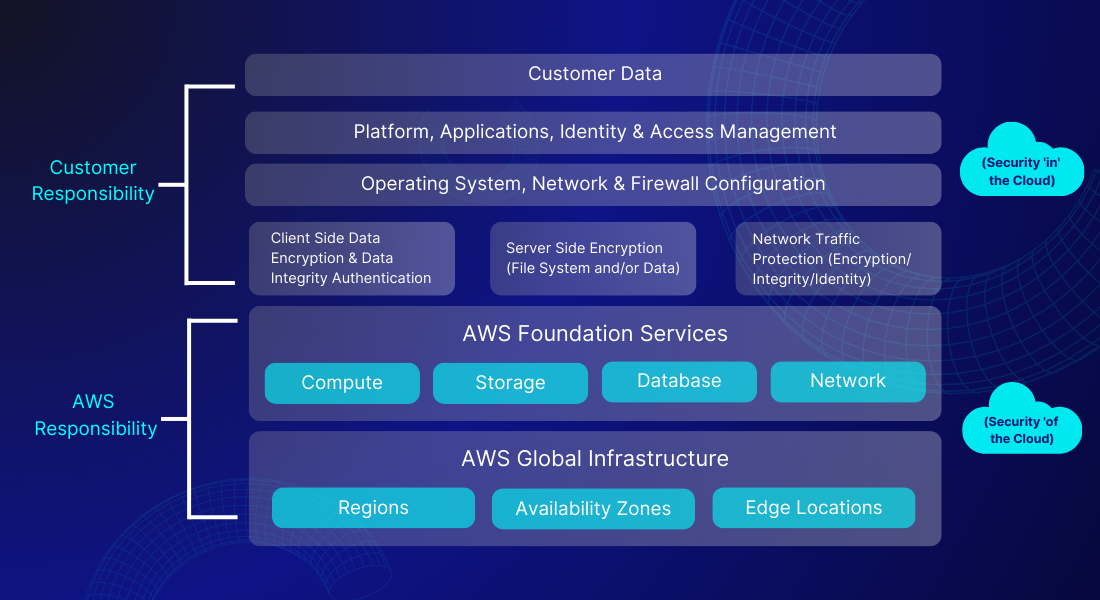
AWS assumes responsibility for global infrastructure components, encompassing regions, availability zones, edge locations, and core services like compute, storage, database, and network. This responsibility extends to controlling access to their data centers where customer data is stored, including physical security measures such as hardware access, networking components, and facility infrastructure like generators, UPS systems, PDUs, CRAC units, and fire suppression systems. This physical access control influences security compliance controls.
Nevertheless, once data is transferred ‘into’ the cloud, the responsibility transitions to the customer. This entails tasks such as implementing encryption for data at rest and in transit, securing the operating system, network, and firewall configurations, as well as managing application security and identity/access.
Note:
Customers can decide on additional security measures, but it’s wise to enhance security to reduce external threats. Although AWS provides robust security controls, it’s ultimately the customer’s responsibility to implement and manage them effectively.
B. Amazon Shared Responsibility Model for Container Services
A container service facilitates the simultaneous operation of multiple applications, allowing them to utilize shared resources on the same operating system. Typically managed by AWS, these services operate on the underlying EC2 infrastructure.
AWS container services include
- AWS Relational Database Service (RDS)
- AWS Elastic Map Reduce (EMR)
- AWS Elastic Beanstalk
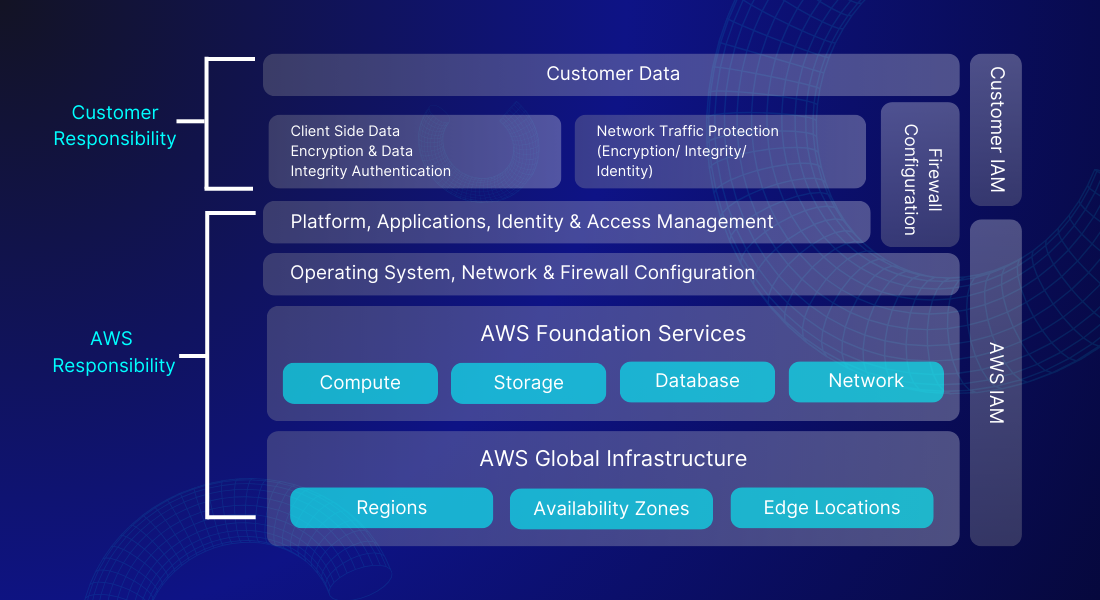
Right off the bat, we can see that AWS now handles platform and application management, as well as the operating system and system/network setup, which used to be your job as a customer. This marks a significant change from the traditional infrastructure-based service. For example, using AWS container services is like using a smartphone. AWS handles the infrastructure, but users must secure their data with firewall settings and access controls.
Note:
Some responsibilities remain with the user. Configuring firewalls is still their job, especially in platform and application management. For example, with RDS, as a customer, we’re responsible for setting up security groups to manage firewall settings.
C. Amazon Shared Responsibility Model for Abstract Services
An abstract service, like storage, database, or messaging services, is entirely managed by AWS. However, customers still own certain configuration aspects and the data they send to or host on the service.
Here are some examples of abstract services:
- Simple Storage Service (S3)
- DynamoDB
- Amazon Glacier
- SQS
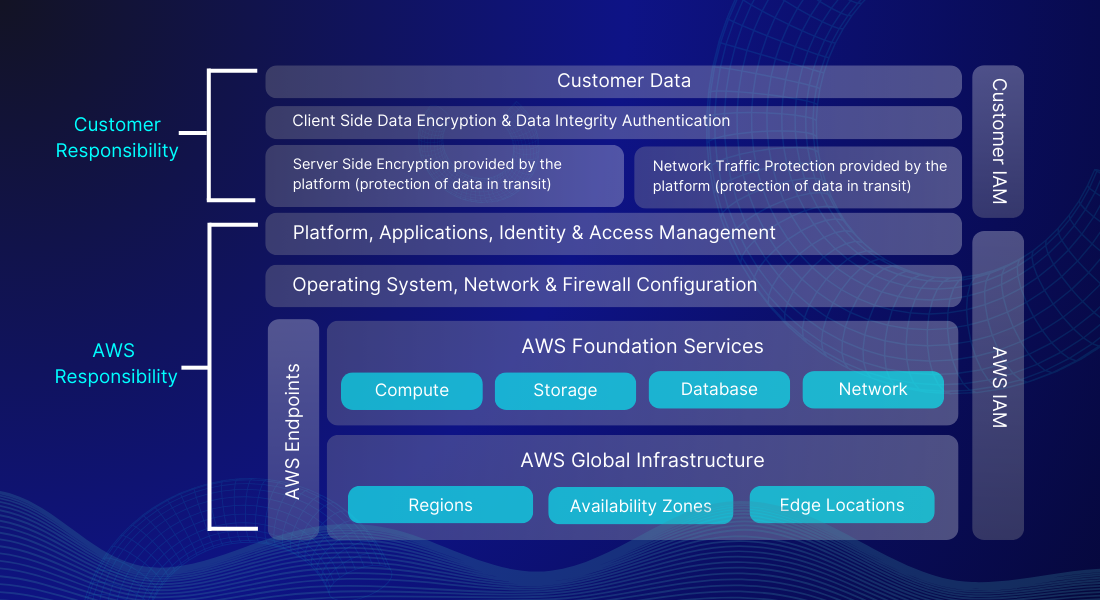
You’ll see that AWS now takes on even more responsibility, like managing network traffic protection using its platform. However, you still need to use IAM tools to set the right permissions, both at the platform level (like S3 Bucket policies) and for IAM users/groups.
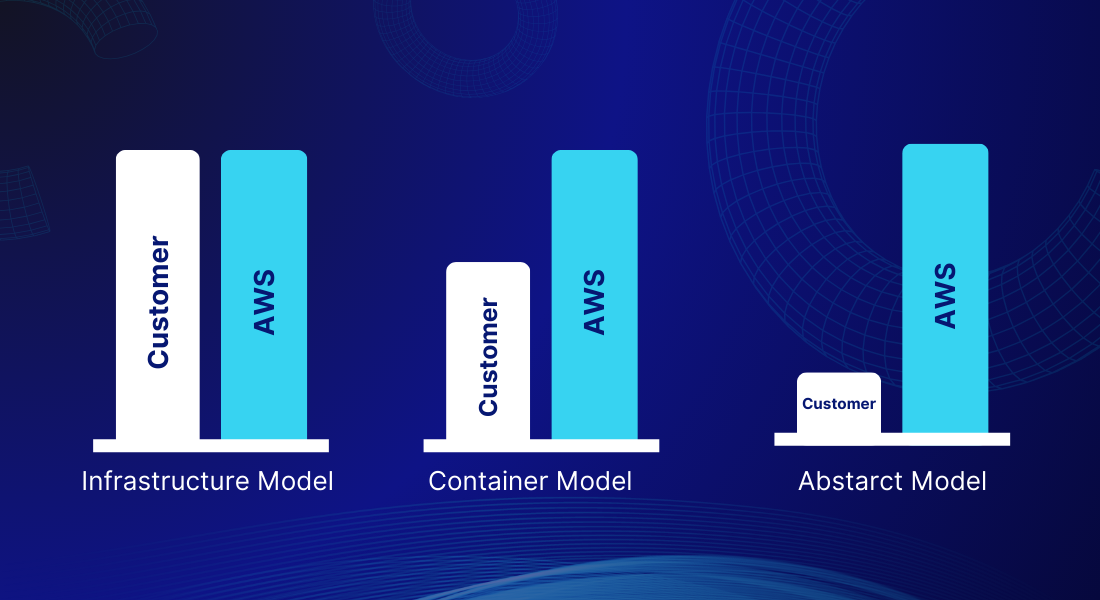
As we see, it’s evident that AWS is taking on more control and responsibility than the customer.
Leverage our AWS Managed Services & reinforce your AWS environment under the AWS shared responsibility model today!
Addressing Challenges in the Amazon Shared Responsibility Model
Here are the potential challenges you might face implementing the Amazon shared responsibility model.
🟠 Lack of Clarity
Many cloud customers lack an understanding of the AWS shared responsibility model, leading to misconceptions about security responsibilities.
Solution: Clear communication and education about the Amazon shared responsibility model to ensure customers understand their security responsibilities.
🟠 Lack of Cloud Expertise
Rapid cloud adoption due to COVID-19 has outpaced organizations’ ability to develop expertise in managing cloud infrastructure.
Solution: Invest in training and development programs to enhance cloud expertise within organizations, or consider leveraging external expertise through managed service providers.
🟠 Native Tools Challenges
Customers face difficulty in finding effective cloud-native security solutions to manage their share of security responsibilities.
Solution: Collaborate with AWS and third-party vendors to develop and implement robust cloud-native security with the help of AWS development tools tailored to address customer Requirements.
🟠 Lack of Ownership
The introduction of cloud security raises questions about ownership within organizations, involving multiple divisions and roles.
Solution: Establish organizations’ clear ownership and accountability frameworks to implement cloud security measures effectively.
🟠 Multi-Cloud Security
Organizations deploying multiple cloud environments face challenges with cloud-specific security tools, varying maturity levels, and lack of coverage for multi-cloud use cases.
Solution: Adopt unified multi-cloud security solutions that provide centralized visibility and management across different cloud platforms, addressing shared responsibility requirements comprehensively. This approach aligns with the AWS shared responsibility model, ensuring that security responsibilities are appropriately managed across all cloud environments.
Applying the AWS Shared Responsibility Model in Practice
Here are the steps for implementing the AWS shared responsibility model:
🟠 Assessing Security Requirements
The first step in implementing AWS shared responsibility models is understanding external regulations and internal policies, which is vital for compliance and data protection. External rules, like GDPR, mandate specific data handling procedures, while internal policies may include encryption standards. Identifying these requirements ensures effective security measures.
🟠 Utilizing Established Frameworks
Industry standards such as NIST CSF and ISO 27017 provide comprehensive guidelines for managing cybersecurity risks. NIST CSF emphasizes a risk-based approach, while ISO 27017 offers cloud-specific best practices. When implementing the Amazon shared responsibility model, aligning with these frameworks standardizes practices and boosts security.
🟠 Leveraging AWS Frameworks
AWS offers CAF (Cloud Adoption framework) and an AWS Well-Architected Framework to streamline cloud adoption and optimize architecture. CAF provides a structured migration approach, while the Well-Architected Framework focuses on security and performance. Utilizing these frameworks when applying Amazon’s shared responsibility model ensures secure and resilient cloud environments.
🟠 Evaluating AWS Security Services
AWS offers IAM and Security Hub to manage access and monitor cloud environments when implementing AWS shared responsibility framework. IAM enables granular access control, while Security Hub provides centralized threat detection. Assessing and utilizing these services enhances security posture and threat response capabilities in alignment with the AWS shared responsibility model.
🟠 Reviewing Third-Party Audits
The Third-party audits like AWS SOC report detail AWS’s security controls and compliance posture when implementing the Amazon shared responsibility model. Reviewing these reports helps understand shared responsibility in maintaining a secure environment and identifies compliance gaps within the AWS shared responsibility model.
🟠 Performing Well-Architected Reviews
Conducting a Well-Architected Review assesses cloud workloads against best practices. You can also use the AWS Well-Architected Tool to identify areas for improvement and implement additional security measures to ensure continuous enhancement of security posture when implementing the AWS shared responsibility model.
🟠 Engaging AWS Security Competency Partners
AWS Security Competency Partners offers specialized expertise in securing cloud environments. Leveraging their knowledge ensures effective navigation of cloud security complexities and achievement of security objectives.
Sharing Your Responsibilities
Understanding your responsibilities for security is crucial when utilizing AWS. While AWS provides default security settings, they may not suffice for your organization’s needs. Activating the right security controls to protect your data effectively is essential. AWS offers various security features, like multifactor authentication, but it’s up to you to enable them.
However, our AWS Consulting Services align closely with the AWS shared responsibility model. We conduct security assessments, implement security controls, provide continuous monitoring, offer security training, and assist with incident response. Our deep proficiency and extensive expertise assure your AWS infrastructure’s security, compliance, and resilience against potential threats, enabling you to concentrate on your core business objectives with assurance.
Frequently Asked Questions (FAQs)
Indeed, AWS offers tools and services to assist customers in effectively detecting, investigating, and responding to security incidents.
Yes, the Amazon Shared Responsibility Model applies to all AWS services, although the specific responsibilities may vary depending on the service’s nature.
Customers are encouraged to frequently review and update their security configurations to align with evolving threats, industry regulations, and shifts in their business needs.
By clearly defining security responsibilities and offering transparency, the Shared Responsibility Model instills confidence in customers that their data and workloads are protected effectively in the AWS cloud environment.
Your Success Is Guaranteed !
We accelerate the release of digital product and guaranteed their success
We Use Slack, Jira & GitHub for Accurate Deployment and Effective Communication.