| Parameters | DevOps | DevSecOps |
|---|---|---|
| Purpose | Focus on increasing speed and software development and delivery | Focus on a secure software development process with security integration throughout the SDLC |
| Team | Only Developer and Operations Teams Work Together | Developer, Operations, and Security: All Teams Work Together |
| Process | The process generally includes CI/CD | The process includes CI/CD along with Security |
| Vulnerabilities | Crafted for IT operations and service management | Versatile for all size of businesses |
| Languages | Not always addressed throughout SDLC | Addressed throughout the SDLC |
| Security Tools | Does not include security tools | Include security tools like Veracode, Burp Suite, OWASP ZAP Proxy |
Summary:
In the digital era, the security of your web apps is paramount to the success of your business. Whether you are a small business owner or a large enterprise, your growth depends on maintaining user satisfaction, which is proportional to the security of your web apps. Considering these facts, in this blog post, we will discuss DevSecOps, its fundamentals, best practices, tools, and the impact of security practices within the DevOps realm. Also, we will shed some light on the difference between DevSecOps vs DevOps, along with the business industries that use it for their web applications’ effective performance and security.
Table of Contents
What is DevSecOps?
DevSecOps is a method used in the world of software development that blends three key components: “Dev” for Development, “Sec” for Security, and “Ops” for Operations. In simple words, DevSecOps is an approach that focuses on security at every stage in the software development lifecycle, from the initial planning and design phases to testing and eventual deployment.
The primary objective of DevSecOps is to integrate security measures into the rapid software release process seamlessly. By doing so, it works to minimize the risk of security vulnerabilities and breaches in modern software applications. Think of it as a comprehensive guide that enhances the safety and reliability of software products.
Benefits of DevSecOps for Businesses
Now that we know about DevSecOps. Let’s see how it helps businesses. Many business owners wonder if it is good for their company, and the answer is a big “YES!” Bringing DevSecOps into the Software Development Life Cycle (SDLC) changes how everyone thinks about security and responsibility. Now, let’s check out some big advantages for business owners that can make their web applications more secure and efficient.
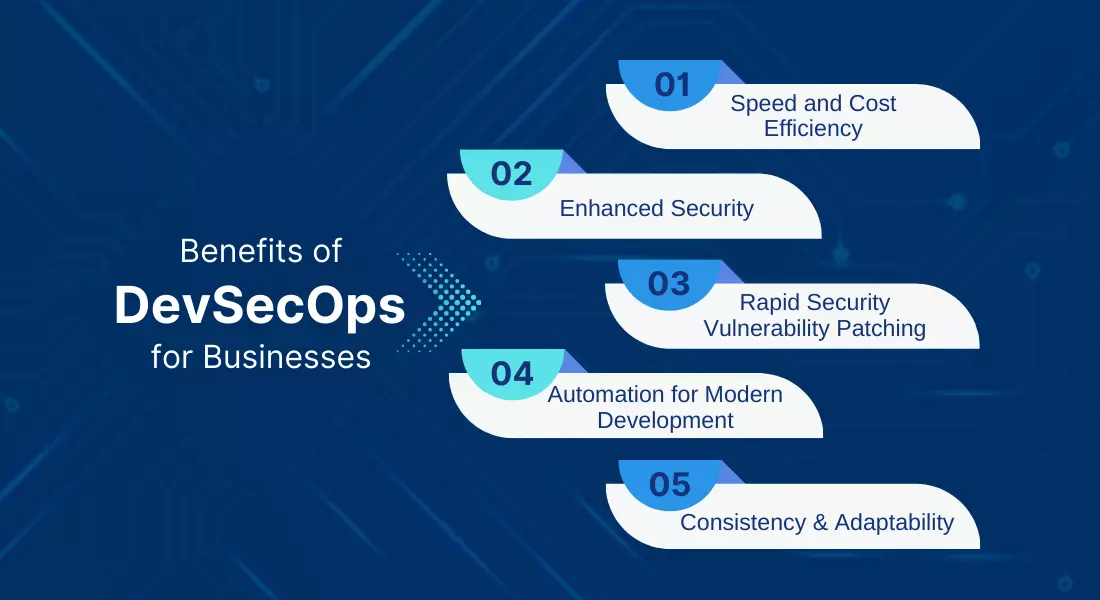
1. Speed and Cost Efficiency
In the highly competitive market, business owners must distinguish themselves by achieving swift development while incorporating the most up-to-date features and updates into their web applications. A strong emphasis on security within the agile team allows organizations to deliver cutting-edge application features and identify issues early in development. This approach minimizes developers’ need to revisit the entire code post-development to address problems, resulting in a more efficient and cost-effective development process.
2. Enhanced Security
DevSecOps, as the name implies, incorporates cybersecurity practices into the software development lifecycle (SDLC). This approach involves real-time code review, audits, scans, and security testing to identify and address vulnerabilities swiftly. This leads to a more cost-effective security posture as protective technologies are integrated. Integrating security measures into the SDLC ensures ongoing code evaluation and analysis, proactively identifying and resolving vulnerabilities early in the development process, thus effectively addressing pertinent concerns.
3. Rapid Security Vulnerability Patching
Another crucial aspect that highlights the crucial benefits of DevSecOps in the SDLC is its capacity to efficiently handle recently discovered security vulnerabilities. It incorporates conducting vulnerability scans and applying patches within the release cycle, reducing the exposure window for potential attackers seeking to exploit known vulnerabilities in public-facing production systems.
4. Automation for Modern Development
Integrating cybersecurity testing into the automated test suite for operations teams proves highly effective in organizations practicing continuous integration and utilizing a continuous delivery pipeline for software releases. The level of automation in security checks varies based on project and organizational goals. Automated testing verifies the inclusion of appropriate, up-to-date software dependencies, validates security unit testing, and conducts static and dynamic analyses to secure the code before the final update reaches production.
5. Consistency and Adaptability
As organizations expand, their ability to address security issues and maintain a consistent approach to mitigating security vulnerabilities becomes paramount. This approach guarantees that security remains consistent throughout evolving environments, adapting to new requirements. A well-developed implementation of DevSecOps includes robust automation, configuration management orchestration, containerization, immutable infrastructure, and serverless computing environments.
Leverage our DevSecOps Consulting Services to Get the Next-Gen Security Solutions You Need For Your Next Project.
Components of DevSecOps
As we have discussed previously, DevSecOps stands out as the optimal approach that can advantage organizations and enhance the security of their web applications. However, realizing the actual benefits of DevSecOps involves a few core components to assure the security of your web applications:
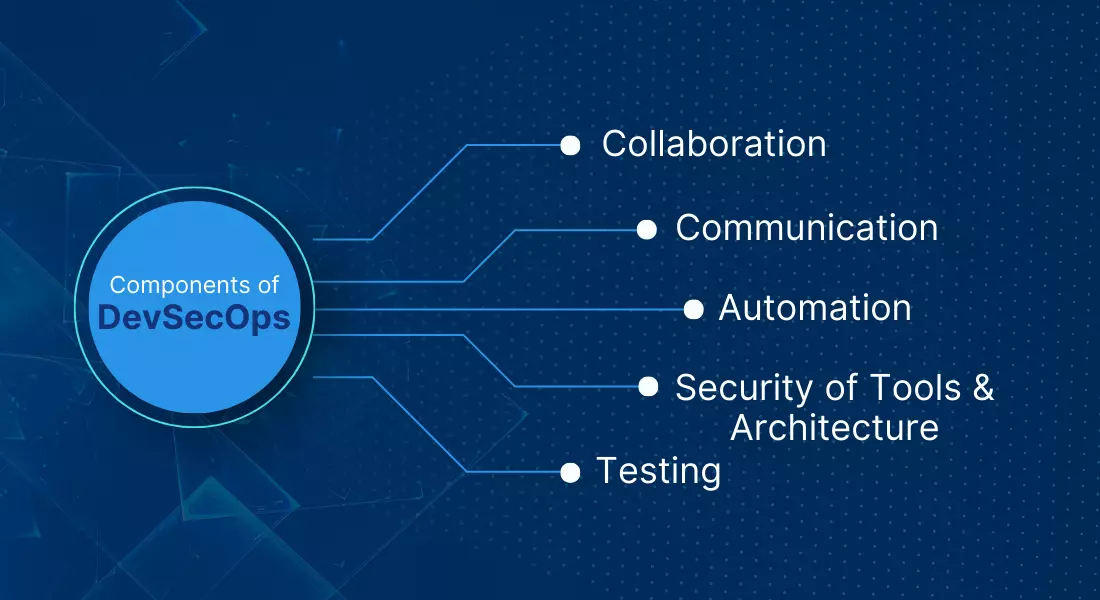
Collaboration
Collaboration is the cornerstone of the DevSecOps approach, reshaping the security landscape by distributing responsibility across development and operations teams and eliminating the need for a separate security team. It plays a pivotal role in efficiently executing essential steps for rapid, high-quality, and secure software development while fully adhering to stringent security requirements.
The security team takes the lead in integrating security standards across the development process, encompassing all application development life cycle phases. This includes automating security tasks and gradually delivering security features, seamlessly integrating them into the software development workflow.
Developers are encouraged to acquire expertise in security standards, relevant tools, and heightened threat awareness to advance this collaborative approach. This collective effort strengthens the overall security stance and expedites the production of secure software.
Communication
As the saying goes, effective communication is essential, making it imperative to bridge the gap between these two facets. Security professionals should convey the importance of control and compliance in language that developers readily understand. For instance, discussing security risks related to project delays and unplanned additional work with developers underscores the significance of addressing these risks.
In turn, developers must grasp security-related responsibilities to become proactive contributors to a more secure and compliant organization. These responsibilities include recognizing potential security risks and adopting best practices when writing code. Additionally, developers should be ready to conduct vulnerability testing during the development process, promptly rectifying any flaws as they come to light.
Automation
Automation is a pivotal element within the DevSecOps framework, crucial in its successful implementation. It seamlessly integrates security into the development process, eliminating potential obstacles for development teams. Automated security testing and analysis can be seamlessly incorporated into the CI/CD pipelines, ensuring the delivery of secure web applications without disrupting innovation and development workflows, thus fostering alignment between developers and security teams.
Furthermore, automation facilitates the implementation of valuable security controls, such as the ‘break the build’ mechanism. This security failsafe system relies on an automated risk-scoring approach that promptly notifies relevant parties when the risk surpasses predetermined thresholds. In such instances, all construction processes halt until developers rectify the identified security issue. Once the security concern is addressed, developers can resume the build process and deliver the application.
Security of Tools and Architecture
To ensure secure software, it begins with a safe DevOps setup. Safeguarding your tools, access, and architecture is vital. Security teams should lead the way in selecting and checking security tools before widespread use.
Manage user access carefully, using techniques like multi-factor authentication, least privilege, and just-in-time access. Segment your CI/CD pipelines to limit unauthorized movement and remove unnecessary accounts.
In a DevSecOps approach, security and compliance are ingrained across all environments, including the cloud. Regularly monitor workstations and servers, scan for vulnerabilities, and apply patches. Automated tools scan code for sensitive data, and new virtual machines and containers come with predefined security settings. Centralized storage keeps your DevOps tools and secrets safe, with encryption and multi-factor authentication for added security.
Testing
Security tests were traditionally the last step right before releasing a product. However, for more effective results, it’s crucial to integrate testing throughout the entire development process. Keatron Evans highlights the value of this approach, suggesting that developers should perform basic OWASP top-ten testing during development to address a substantial portion of cybersecurity issues rather than waiting until the app is fully built.
Automation is essential to ensure security keeps pace with development. Automation simplifies processes such as code scanning to identify sensitive information before it’s added to repositories, preventing passwords from appearing in event logs, and detecting malicious code within applications.
A robust testing strategy should incorporate a mix of techniques, including Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and periodic but equally important methods like penetration testing, Red Teaming, and Threat Modeling. These approaches provide insights from a hacker’s perspective without disrupting the production environment. Some organizations even encourage thorough testing through “bug bounty” programs, offering rewards for reporting potential security issues.
Top 5 DevSecOps Best Practices
There are many benefits of DevSecOps for business owners. However, organizations must implement several DevSecOps best practices to improve their security and leverage it to its optimal potential. Here are a few examples:

1. Shift Left Security
“Shift Left Security ” focuses on moving security practices earlier in the software development lifecycle (SDLC), particularly during the planning, design, and development stages. This approach emphasizes integrating security measures at the very outset of a project. By doing so, potential vulnerabilities and weaknesses are identified and addressed as early as possible, reducing the likelihood of costly security issues arising later in the development process. For example, during the planning phase, security considerations are part of the project requirements, ensuring security is a fundamental aspect of the development process.
2. Security Education (Shift Right)
“Security Education” in the context of “Shift Right” implies extending security considerations beyond the development phase and into the operational and maintenance phases of an application’s lifecycle. This practice ensures that security remains continuously focused throughout the application’s life. It involves implementing security monitoring in operational environments to detect and respond to real-time security incidents. It may also include conducting regular security assessments to ensure the application remains resilient against evolving threats. Security awareness training for all employees is also part of this approach, making security a shared responsibility across the organization.
3. Automated Security Tools
“Automated Security Tools” streamline security processes by leveraging software applications that automatically perform security testing and scanning. These DevSecOps tools are designed to save time, enhance efficiency, and improve the consistency of security checks. For instance, static analysis tools can automatically scan code for vulnerabilities, while dynamic analysis tools assess the application’s security in real-world scenarios. Penetration testing tools simulate actual attacks to identify weaknesses, and vulnerability scanners proactively search for known security issues. Organizations can promptly identify and remediate security concerns by automating these security checks without requiring extensive manual intervention.
4. Cultivating a Security Culture
“Cultivating a Security Culture” focuses on fostering an environment where security is a shared responsibility across the organization. It goes beyond just implementing security measures and encourages every organization member to actively participate in protecting assets and information. This cultural shift includes providing security training to employees, effectively communicating security policies and procedures, and encouraging the reporting of security incidents. When everyone within the organization understands the significance of security and takes responsibility for it, the overall security posture is significantly enhanced.
5. Tracking, Auditing, and Visibility
These are essential to maintaining a solid security posture. This involves continuous monitoring, auditing, and maintaining visibility into the security of applications and infrastructure. For instance, security monitoring and logging are crucial for capturing events and incidents in real-time. Regular security assessments help evaluate the current security state of systems and applications, and various security tools provide visibility into the security of applications and infrastructure. This data can be used to identify and mitigate security risks, ensuring that an organization is well-prepared to respond to potential threats and vulnerabilities.
Application Security Tools Used in DevSecOps
The DevSecOps tools play a vital role in application security, which organizations can use to find and fix security issues in the early stages of development, making it harder for attackers to exploit their applications. Let us have a glimpse of these four tools in detail to understand better:
Static Application Security Testing (SAST)
These specialized DevSecOps tools delve into an application’s source code, meticulously searching for security vulnerabilities. They excel at pinpointing common issues such as SQL injection, cross-site scripting, and buffer overflows. Their primary use case is during the early stages of development when the code is being written and tested.
Software Composition Analysis (SCA)
SCA tools look closer at an application’s software components, including libraries and frameworks, focusing on identifying well-known security flaws. This analysis helps to uncover vulnerabilities that might be introduced when third-party components are integrated. SCA tools primarily come into action in the early stages of development, especially during the planning and design phases.
Interactive Application Security Testing (IAST)
IAST tools offer dynamic assessments of running applications to identify security issues, especially those that can be elusive for SAST or SCA tools. They typically play a critical role during the testing and deployment phases when the application is operational, and interactions between its components must be scrutinized.
Dynamic Application Security Testing (DAST)
DAST tools evaluate applications from an external perspective, effectively simulating an attacker’s tactics. These tools prove invaluable in detecting vulnerabilities that malicious actors could potentially exploit. DAST tools are predominantly employed during the testing and deployment phase when a live, externally accessible application needs to be thoroughly assessed for security.
DevOps Vs DevSecOps: A Brief Comparison
The difference between DevOps and DevSecOps are essential paradigms in software development, with each having its unique focus and methodology. Let us look at both of them.
DevOps
As the name suggests, DevOps stands for ‘Development’ and ‘Operations.’ It revolves around optimizing the collaboration between development and IT operations teams. The core behind DevOps is to expedite the software development process, emphasizing automation and CI/CD for faster software delivery. In simple terms, the traditional approach to security comes into action as a separate or secondary concern addressed at a later stage. The prime focus here is speeding up the software delivery, whereby security is an external component.
DevSecOps
In simple terms, DevSecOps is an evolution of DevOps focusing on security. It represents a fundamental shift in software development by making security a fundamental and inseparable part of the entire SDLC. DevSecOps brings developers, IT operations, and security teams together to collaborate from initial planning and coding phases to testing and deployment. Security here is not an afterthought but a top priority. In this approach, you’ll find practices like automated security testing, continuous monitoring, and shared responsibility for security across all teams. The ultimate goal of DevSecOps is to create more secure applications by making security a central and inherent aspect of the entire development process.
Therefore, comparing DevOps vs Dev Sec Ops enables us to infer that the only difference between the two is including “Security” as a core element. While DevOps mainly focuses on improving software delivery through automation and collaboration, DevSecOps takes this further by prioritizing security, cultivating a security-first culture, and ensuring that security is an integral part of the development journey from inception to deployment. This approach results in a more secure software environment where the combined efforts of all teams contribute to the protection of digital assets.
Industries Benefiting from DevSecOps
DevSecOps is a dynamic approach that brings security to the forefront of the software development process, making it a valuable asset in various industries. Its emphasis on the security aspect of software development makes it a critical tool in mitigating cybersecurity risks and protecting critical assets in the rapidly evolving technological landscape. Let us glimpse how DevSecOps is particularly advantageous in specific sectors:

Automotive
In the automotive industry, integrating software into vehicles is a growing trend. DevSecOps plays a crucial role in ensuring the security and safety of these embedded systems. It helps in early detection and mitigation of vulnerabilities, reducing the risk of cyber-attacks on vehicles. Moreover, as autonomous and connected vehicles become more prevalent, DevSecOps is vital in safeguarding these advanced technologies.
Finance, Retail, and Ecommerce
The finance, retail, and Ecommerce sectors handle vast amounts of sensitive customer data and financial transactions. Security breaches can have severe consequences, including financial losses and damage to reputation. DevSecOps is instrumental in preventing security breaches by integrating security into every application development and deployment stage, providing a proactive defense against cyber threats.
Healthcare
Healthcare relies heavily on the secure handling of patient data and the operation of critical medical devices. DevSecOps is essential in ensuring that healthcare software and systems are robust, compliant with privacy regulations, and protected against cyber threats. It also facilitates rapid response to emerging security concerns, protecting patient safety and data.
Embedded Devices and IoT
As the Internet of Things (IoT) and Embedded Systems ecosystem grows, the security of connected devices and embedded systems is a top priority. Dev Sec Ops is valuable in addressing security challenges in this sector. It assists in identifying and mitigating vulnerabilities in embedded software and protecting against data breaches, device manipulation, and other cyber-attacks.
Conclusion
We can now simply state that DevSecOps is a pivotal shift in software development, emphasizing security integration throughout the entire development lifecycle. This approach encourages collaboration, automation, and continuous monitoring, effectively identifying and mitigating vulnerabilities early in the process, reducing the risk of security breaches, and minimizing associated costs.
In a world where security is paramount, DevSecOps is not merely a trend but a necessity. By adopting this mindset, organizations can build and deploy software that meets business requirements, safeguards valuable data, and maintains user trust. It’s time for developers, operations professionals, and security experts to embrace DevSecOps and make it an integral part of the software development journey for a more secure digital future if you are also a business owner looking for professional DevSecOps Consulting Services.
Hire DevOps Engineer from Bacancy to achieve exceptional efficiency of our DevSecOps Consulting Services and leverage the power of DevSecOps methodology with unmatched security and efficiency.
Frequently Asked Questions (FAQs)
Commonly used tools encompass static and dynamic code analysis, vulnerability scanning solutions, security information and event management (SIEM) systems, and identity and access management solutions.
Challenges may include resistance to change, the quest for security expertise, and ensuring security practices do not impede development.
No, DevSecOps principles are adaptable to various applications, from legacy systems to on-premises software.
DevSecOps plays a vital role in fulfilling compliance requirements by continuously monitoring and addressing security issues, often mandated by regulations such as GDPR and HIPAA.
A DevSecOps Engineer helps teams work together to make software efficiently. They use automation, set up systems to quickly test and release code, and ensure security is built into the process. They play a crucial role in speeding up software development and making it more reliable.
Your Success Is Guaranteed !
We accelerate the release of digital product and guaranteed their success
We Use Slack, Jira & GitHub for Accurate Deployment and Effective Communication.