Quick Summary:
Node.js is the most preferred and popular JavaScript framework for web application development among business owners and developers. However, you require Node js best practices for enhancing your web applications. This blog contains various practices, such as practices to build node js apps, error handling, security tips, and production.
Table of Contents
Introduction
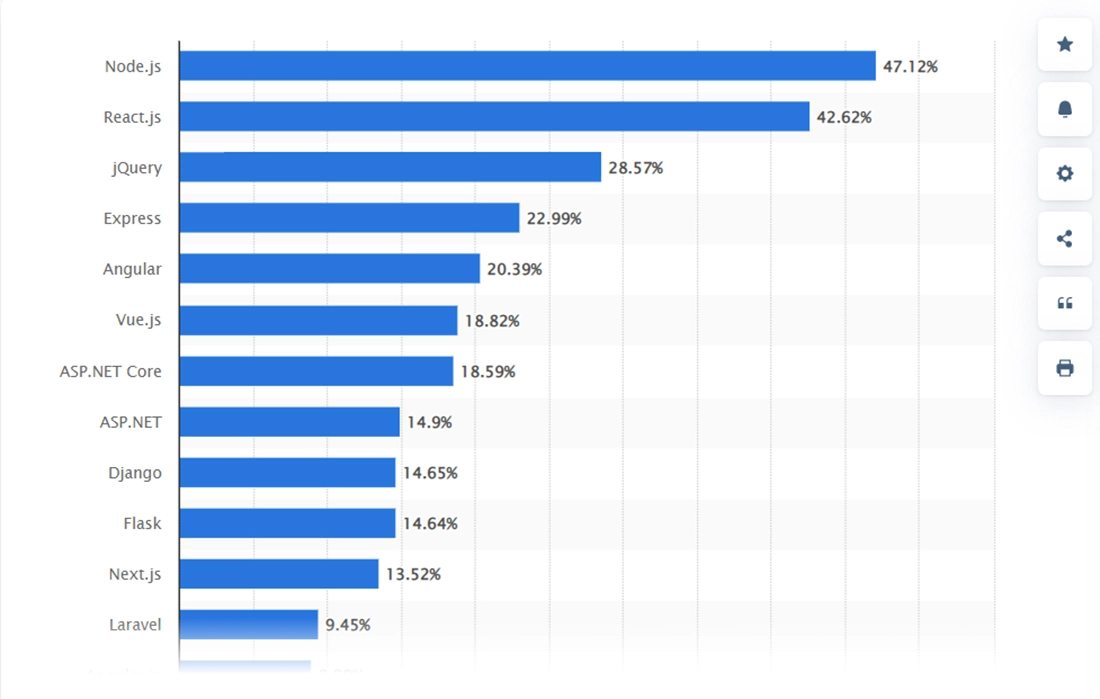
According to the statistics by Statista, Node.js stands at the top of the list of the most popular frameworks compared to the other popular frameworks available within the market.
Node.js is a lightweight and scalable network-driven app framework built on an asynchronous event-driven JavaScript runtime. It is based on Chrome’s V8 JavaScript engine. The framework allows for horizontal and vertical scaling and building client- and server-side applications. Also, it is a popular framework for its speed and efficiency in development.
However, with numerous beneficial features, there are complexity and errors to deal with. Hence, we have curated Node js best practices to get the most out of your Node.js application. First, let’s delve into Node.js best practices for building Node js applications.
Top 12 Node Js Best Practices to Build Node.js Apps in 2024
Following are the NodeJS best practices that can help to build scalable and efficient applications quickly and effectively.
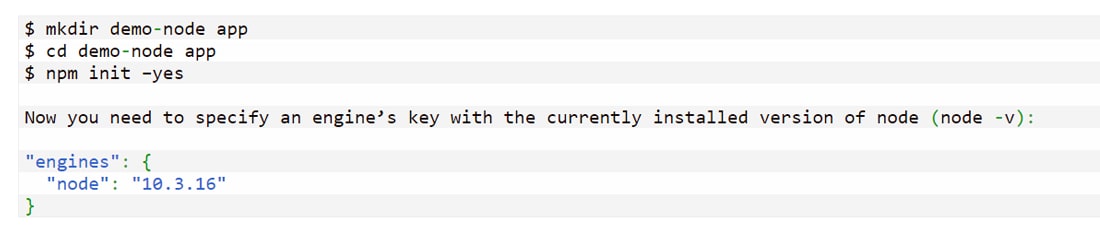
1. Start Your Project With npm init
Whenever you start with a new Node.js project, create a package.json file to manage your dependencies and project configuration. This file contains metadata about your project, such as name, version, and dependencies. The core benefit of using this is that it makes managing your project’s dependencies easier and helps other developers quickly understand your project’s structure and requirements.
You can use the ‘npm init’ command to create a package.json file and add dependencies to your project. Once you have the package.json file using the npm init, you can use the ‘npm install’ command to install all the dependencies listed within the file.
It lets you easily specify which dependency version to use and ensures that everyone working on the project has the same dependencies installed. This can help avoid compatibility and version mismatches issues, saving time and keeping your project organized.
2. Use a Node.js Style Guide
A Style Guide is an essential Node js best practice to maintain consistency and readability in your codebase. It also ensures that your code is easily understandable for you and the other developers.
A precise set of guidelines enable the developers to follow a consistent code style, naming conventions, and formatting throughout the project. It saves time and reduces errors while working on larger node js projects with multiple developers.
3. Use Environment Variables
These allow you to separate the configuration from the code. The dynamic values can be set outside of your application’s code and accessed by your application at runtime. Using environment variables allows you to store sensitive information such as database credentials, API keys, and other configuration parameters without exposing them in your codebase.
Use the Below commands to set default values via the Npmrc file:
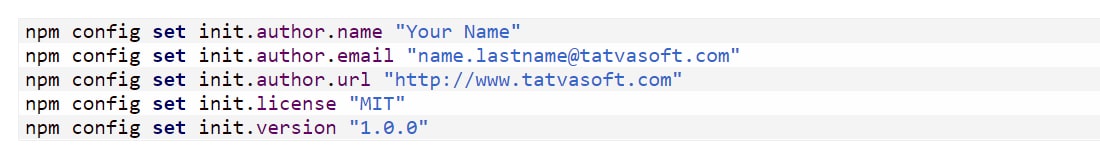
You can access the environment variables in Node.js using the ‘process.env’ object. To set the environment variables, you can choose between the available methods based on your operating system deployment environment. A few standard methods are setting them in the ‘.env’ file or your hosting provider’s dashboard.
4. Go Asynchronous
As we know, Node Javascript runtime possesses a single-threaded nature meaning too many synchronous functions can lock the functions that can affect the performance of your web application. The asynchronous structure here helps to make your code free from blockages and ensure efficient use of the system resources.
You can use the asynchronous code whenever possible. However, to get the best out of the asynchronous method, you must ensure and follow a few of the NodeJS Best Practices, such as using asynchronous functions and callbacks, utilizing Promises or async/await, limiting concurrency, and implementing error handling techniques.
5. Automatic Application Restart
Ensuring the smooth functioning of your Node.js application in the event of crashes or errors is crucial, and automatic restarts are an essential best practice. Tools like PM2 or Forever can monitor your application and automatically restart it if needed, preventing downtime and lost revenue. Similarly, nodemon can monitor your code in real-time, keeping your application running even when changes are made. You can quickly diagnose and fix issues by properly logging errors and exceptions with a framework like Bunyan or Winyan.
6. Require All Your Dependencies Upfront
Loading and organizing your dependencies upfront allows you to avoid issues arising later in the development process or after your application has gone live. This can help you identify potential issues earlier in the development cycle and prevent them from becoming bigger problems.
Additionally, requiring upfront dependencies can help with code readability and maintainability, making it easier to understand your code’s external dependencies.
7. Keep Your Code Clean And Light
Keeping your Node.js code clean and light is essential to maintain the code quality and reduce the possibility of introducing bugs. One of the Node js best practices is to follow the “Single Responsibility Principle,” which means that each module or function should only be responsible for one task.
You should also nest your code sparingly or overly complex, as this can make it hard to read and debug. Instead, use asynchronous functions or promises to reduce your code and make it more readable.
8. The Gzip Compression
Nowadays, most clients and servers support Gzip. The server compresses the response time when a gzip-compatible browser requests a resource, reducing latency and time lag. Gzip can improve your application’s performance when you request remote servers and respond to clients.
9. Git The Substantial Bits
Every application comprises generated and essential files. It is advisable to avoid tracking anything formed using source code like Git, as it leads to excessive noise in your Git history when you track generated files.
10. Client-Side Rendering
Due to Model-View-Controller frameworks like AngularJS and BackboneJS, creating dynamic page applications has become much easier. Using client-side rendering in Node Js will radically save bandwidth and reduce latency.
11. App Monitoring
How does it sounds to get notified when something goes wrong with your application sound? You don’t want to get aware from social media feeds or thousands of angry users that the application has not been functioning correctly for a few hours now. So occupying something to alert at the time of critical issues is essential.
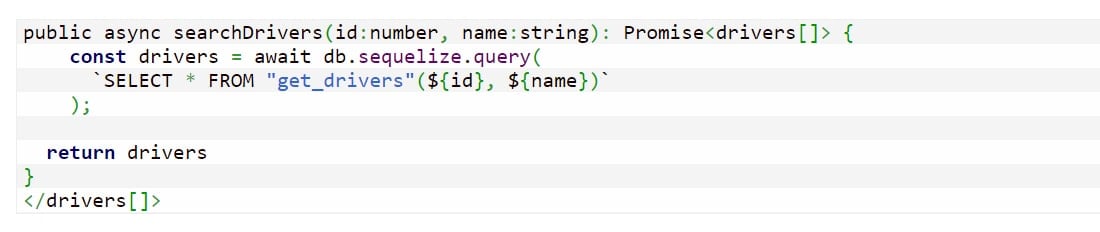
12. Stop SQL Injections
The risk of database manipulation increases whenever JS strings are frequently used. Built-in parameters for queries given by object-relational mapping should be used to stop SQL injections.
13. Code Validation
Testing is an obvious point, and it will save you on many occasions. In-between the development, it happens when the first few production issues occur. You wish you could have done a few tests in the first place. So, start developing the habit of testing and experience a smooth and bug-free application performance.
Do you dream of creating extraordinary user experiences that leave your competitors in the dust?
Look no further! Hire Node.js Developer to level up your Node.js projects and build exceptional applications that dazzle your users and drive success.
Top 6 Node Js Best Practices for Error Handling in 2024
Error handling is critical to Node.js development, as errors can lead to unexpected behavior and even security vulnerabilities. However, if you follow the given Node js best practices, it will become easier for you to handle those errors.
🟠 Catch Blocks
Implement try-catch blocks to handle errors in synchronous code. It allows you to catch errors and handle them gracefully, rather than allowing the entire application to crash. It’s essential to remember that try-catch blocks should not be used to handle all errors in your application, as they can be resource-intensive.
🟠 Error-First Callbacks
Use error-first callbacks to handle errors in asynchronous code. This involves passing an error object as the first parameter to a callback function, which can be used to handle the error. This approach is widely used in Node.js, and many libraries and APIs follow this convention.
🟠 Central Error-Handling Middleware
Use a central error-handling middleware to catch and handle errors in your application. This middleware can catch errors not handled by other middleware or routes and provide a consistent way of handling errors throughout your application.
🟠 Appropriate HTTP Status Codes
Use appropriate HTTP status codes when returning errors from an API. For example, use a 404 status code for a resource not found an error or a 500 status code for a server-side error. This can help clients understand what type of error occurred and respond appropriately.
🟠 Log Errors
Use a logging library like Winston or Bunyan to log errors. This can help you track down the source of errors and troubleshoot issues. Logging errors can also help you identify potential security vulnerabilities or other issues that must be addressed.
🟠 Test Error Scenarios
Write tests to ensure that error handling works correctly. Test for both expected and unexpected errors, and ensure that errors are handled appropriately and don’t cause unintended behavior.
Top 23 Node.js Application Security Tips in 2024
We have already understood the Node.js best practices for scalable and strong application performance. Now let’s understand the best Node.js application security tips to follow for a secure environment for your application.
1. Use Linter Security
While developing a Node.js application, you may have invoked a child process, used eval, or imported a module with a non-string literal. Linting ensures you eliminate potentially dangerous patterns in your Node js code. You can use the linter plugins like eslint-plugin-security to catch threats and vulnerabilities while coding your node.js application.
2. Apply Rate Limiting on the Middleware
Your application is threatened by a DOS attack where authenticated users may not get the requested or degraded service. To overcome such a situation, you should use middleware for smaller and less-critical apps to implement rare limitations.
You can use rate-limiter-flexible packages, Nginx, cloud firewalls, or cloud load balancers for comparatively larger apps. This is one of the most-useful Node js practices.
3. Secret Management
You must not save your secrets in configuration files or source code to secure node js applications. Unknowingly, you may keep private repositories publicly, where you unveil all your secrets. Following this Node js best practices, anyone can access your APIs, database, services, and more.
Thus, you must use Kubernetes/ Docker secrets, Vault products, or environment variables. In this manner, your secrets are safe, encrypted, and managed.
💡 Pro Tip: Use pre-commits and push hooks to avoid accidental mysteries.
4. Prevent Query Injections
Many developers use JS strings or string concatenations to insert values into queries. However, these Node js best practices invalidate your data, and your app is highly vulnerable to SQL/NoSQL injection attacks. Sequelize, KnexKnex, and Mongoose are the node.js libraries having built-in protection against SQL injection threats.
To prevent these malicious attacks, you must always use Object-Relational Mapping/ Object Document Mapper ORM/ODM or database libraries that support indexed parameterized queries.
5. Evade DOS Attacks by Seting the System Crash
Due to some errors in the Node js requirement, your entire process can crash. In fact, few Node JS best practices suggest preventing the process despite catching the mistake. All this struggle because the attackers get an accessible spot vulnerable to the input and crash the system with repeated faulty inputs.
Though there is no solution to this adversity, you can validate the information and spare the process of hitting on invalid user input. You can wrap all the incoming routes with a catch and ensure that your system doesn’t crash on error requests. By doing so, you provide your node js web application security.
6. Regulate the HTTP Headers
Use secure headers to combat cross-site scripting (XSS), clickjacking, and other malicious attacks that lead to massive node.js application security vulnerabilities. You can use modules like the helmet that is easily configurable and create your node js security tutorial.
7. Examine for Vulnerable Dependencies
One of the Node JS best practices is the NPM ecosystem, which makes it common to have many dependencies for a project. You must always check your dependencies and use tools like Nsp, Snyk, and NPM audit to track, monitor, and patch vulnerabilities. By aligning these tools with the CI setup, you can catch a dependency before it is executed.
8. Use Bcrypt Instead of Crypto
Save your API passwords or secrets using Bcrypt, a secure hash + salt function. Without this function, your passwords or secrets are vulnerable to brute force and dictionary attacks. As you use the Bcrypt process, you specify the number of rounds and the number of times the data works, so it is more securely and forcefully hashed.
9. Escape Output
Often, your browser executes the user-sent input, which is known as Cross-site scripting (XSS) attack. You can use encoding, escaping, or dedicated libraries that mark data as pure content and do not allow it to execute. Hence, you must escape output like HTML, JS, and CSS output, or else the attackers would store malicious code in your DB, which will pass over to needy clients.
10. Validate Incoming JSON Schemas
The attacker may try to find the various input combinations that crash your application. So, don’t be generous and permissive to such experiments and trials. You should lay validation on incoming requests’ body payload and check if it meets your expectations. Jsonschema or joi are lightweight JSON-based validation schemas that you can use to avoid the coding struggle.
Are you ready to step into a world of boundless possibilities with Node.js?
Our Node.js development company boasts a talented group of developers who are passionate about creating outstanding applications. Get in touch with us today and witness the magic of Node.js in action!
11. Backlisting JWTs
Your Node.js application considers JSON Web Tokens (JWT) issued by you as authentic, which makes you accessible to the app data using these tokens. However, in the case of misplaced or stolen tokens, there is no way that you can stop an attacker from accessing your application.
For instance., when you use JWT with Passport.js. Hence, you must validate your untrusted tokens that are expired or misplaced.
12. Prevent Brute-force Attacks Against the Authorization
A hacker can breach your application by trying too many attempts to enter your username and password. You can prevent such brute-force attacks by restricting a particular IP from logging in to your app by implementing rate-limiting authorization.
For instance, when you find consecutive failed attempts of permission of the same username and a unique IP, restrict it further. Or when there are several failed permission attempts for an extended period, like 100 failed attempts by a particular IP on the same day.
13. Run Node.js as a Non-Root User
A user process generally has the least access to the system information and resources. However, with root access, an attacker can attain the maximum power of the local machine and can reroute traffic to other servers. By default, Node.js runs as a non-root user with unlimited access, which is vulnerable. Thus, you must use a non-root user or bake it into a Docker image.
14. Limit Payload Size
As your Node.js application receives larger requests, it has difficulty processing other important work, which leads to lower app performance and exposes your app to DOS attacks. A bigger body payload is under execution by a single thread for large claims. Attackers can pose a threat without multiple requests because of the bigger payload size. You can use express body-parser to limit body size by accepting only small-size payloads.
15. Sidescape the Javascript Eval Statement
A considerable performance concern arises because the eval statement permits executing a custom JS code while running the app. A user may input a malicious JS code, leading to a node.js application security issue. By using the eval function, or the new Function, setTimeout, and setInterval, susceptible text gains access to the page’s Javascript through the input. Hence, you should use such functions cautiously.
16. Counter Malicious RegEx
All JavaScript apps are vulnerable to regular expressions, specifically the Node.js application. They cost large CPU power as the user inputs text to match. Sometimes you may block the entire event loop due to poorly written RegEx.
E.g., the moment package was destroyed in Nov 2017. You should use safe-regex to find out which of your regular expressions pose a threat or use the validator.js package.
17. Safe Module Loading
Keep a check on what your Node.js program is importing or requiring. The fs.readFile() parameters often come from the user input, which can be a malicious act. The impact of such results can access your sensitive resource or breach into other existing file systems. You should use the linter Eslint-plugin-security to catch such vulnerable user attempts.
18. Unsafe Code in a Sandbox
Make sure you use a sandbox tool when your application runs an external code because that can attack your system with infinite loops, overload memory, or access sensitive env variables. You must use dedicated processes like a cluster.fork(), npm packages, or a serverless environment as a sandbox to protect your Node.js application.
19. Caution While Working with Child Processes
Try not to use child processes; when you have to, validate the inputs. They can pose shell injection attacks by unsanitized system commands. Instead, you can use child_process.execFile, which executes a single command with multiple attributes, and thus will not expand shell parameters.
20. Configure 2FA for NPM or Yarn
Hackers can steal the developers’ credentials and instill malicious code in your project libraries, despite applying multifactor authentication (MFA). The entire web may be infected if the attackers plant the code in the public domain. Hence, you must use two-factor authentication 2FA with npm/yarn, which leaves no chance of hackers.
21. Cookie & Session Security
You should not reveal your tech stack because attackers know the weakness of all the frameworks and technologies. Mostly cookies are transmitted over insecure connections, and hackers can tweak the session for private information. You must protect your app as well as your user’s privacy by keeping a check on Cookie and Session security.
22. Prevent Unsafe Redirects
As the attackers know that you are not validating user input, they can pose attacks like credential stealing and launch phishing attacks or other malicious events. Thus, you must take care of all the redirects that arise from your application. If you take this matter lightly, attackers can post specific links to forums or social-media attractions so your users can click through them.
23. Avoid Publishing Secrets
You must see that all your passwords, API keys, and other secrets are safe and not published on the public NPM registries. If not, attackers can leverage the benefits of your leaks and impede your financial losses, impersonating you and other risks. You can use the .npmignore file as a blocklist and the files array in package.json as a safelist.
Top 9 Node.js Production Best Practices in 2024
When developing a production-ready Node.js application, there are many factors to consider. Below are a few top Node.js production best practices to help you build robust, scalable, and secure Node.js applications:
Smart Logging for Increased Transparency
In complex production-ready applications, logs can be a lifesaver regarding debugging. Hence, it is crucial to plan your logs from the beginning and define a proper framework for collecting, storing, and analyzing them. This will ensure that the desired information can be easily extracted when needed.
Lock Dependencies to Specific Environments
Using npm config files like .npmrc can help lock dependencies to specific environments, ensuring that the exact version of each package is saved. This practice can overcome the issue of dependencies moving across different environments by default, which was possible in npm versions before NPM5.
Utilize All CPU Cores for Better Performance
Node.js runs on a single CPU core by default, leaving all other cores unproductive. It is a best practice to utilize all CPU cores to reduce performance bottlenecks. PM2 or Node Cluster can be used for small to medium-sized applications.
In contrast, larger applications may require replicating the process using deployment scripts or Docker clusters based on the Linux init system.
Monitor Node Memory Usage
Node.js has a tricky relationship with memory management, and its v8 engine has some limits on memory usage. Monitoring the memory usage of Node is essential, especially since there are known memory leaks present in Node’s code.
While small apps can use shell commands periodically to monitor memory usage, larger apps should consider using a robust monitoring system to stay on top of memory usage.
Store Front-end Assets in Dedicated Storagex
Storing front-end assets in a dedicated location like S3 or a CDN is a good practice because it can negatively impact Node’s performance when dealing with many static files due to its single-thread model. It is always advisable to store front-end assets in dedicated storage rather than within the Node server.
Use Automated Vulnerability Detection Tools
Even the most renowned dependencies, such as Express, have known issues that can put systems at risk. Commercial and community tools that constantly check the system for vulnerabilities and warnings can quickly rectify this issue. Using such tools can help ensure that vulnerabilities are addressed instantly.
Set NODE_ENV=production
Setting the environment variable NODE_ENV to ‘development’ or ‘production’ are Node JS best practices to indicate whether the production optimizations should be mobilized. Many npm packages discover the current environment and then try to optimize their code for production. Hence, setting NODE_ENV precisely is crucial.
Prefer Using LTS Release of Node.js
Using a Long Term Support (LTS) version of Node.js provides added security as critical bug fixes, security updates, and performance improvements are available longer. Unless there is a strong reason not to do so, using the LTS version of Node.js is advisable.
Always Install Packages with npm ci
Running npm ci is recommended to ensure that production code always uses the same version of tested packages. This command rigidly does a clean install of dependencies based on package-lock.json and package.json, making it suitable for automated environments such as CI/CD pipelines.
Ready to Take Node js Application to Next-Level?
In conclusion, Node.js has grown from a JavaScript library to a strong and independent programming language for building scalable back-end and RESTful APIs. By implementing these Node js best practices, you can ensure optimal performance, security, and reliability for your Node applications.
Several successful companies, including Twitter, Walmart, and Uber, have leveraged Node.js to achieve better results. If you aspire to join their ranks, Hire JavaScript Developer to help you maximize Node.js’s full potential. With the right approach, success is within reach.
Frequently Asked Questions (FAQs)
Always prefer to use a package.json to improve the performance of your Node JS application. Moreover, go Asynchronous and try to use lightweight code for optimal performance.
Because of its single-thread behavior, NodeJs is mainly used for traditional web applications, real-time applications, network applications, and back-end API.
To keep your web application safe and secure from attacks, you should always follow all the Node js best practices and open web security projects (using the Lint plugin, stopping SQL injections )to avoid NodeJS application vulnerabilities.
Your Success Is Guaranteed !
We accelerate the release of digital product and guaranteed their success
We Use Slack, Jira & GitHub for Accurate Deployment and Effective Communication.